Shield Cybersecurity
Unbreakable Cybersecurity for Your Business
The Threat is Real
Cyber threats loom. Breaches cost fortunes and shatter reputations.
Our Shield Cybersecurity
Our Shield Cybersecurity turns vulnerability into invincibility.
Achieve Your Goals
Achieve business goals without cyber threats.
Why risk it?
The Silent Killer Lurking in Your Network
The Devastating Impact
It’s 3 AM. Your phone buzzes—a breach alert. Customer data exposed, operations frozen, regulators knocking. Panic sets in as you calculate the damage: lost revenue, legal fees, shattered trust. This isn’t fiction; it’s the reality for businesses hit by cyber threats every 39 seconds.
The Unseen Threats
Externally, sophisticated attacks from ransomware gangs and state actors exploit every weak link. Internally, it’s the gnawing worry: “Are we next?” At its core, technology should fuel your dreams, not destroy them. As top cybersecurity companies warn, ignoring this villain invites disaster.
Meet Your Cybersecurity Guardian: Leverage IT Consulting
Leverage IT Consulting stands as your steadfast ally in the digital realm. With decades of experience, top-tier certifications, and a track record of transforming digital chaos into calm, we bring unparalleled expertise to secure your business.
24 Years of Experience
We’ve spent 24 years fortifying businesses nationwide, blending cutting-edge tech with unwavering resolve.

Certified Professionals
Our team holds top certifications and aligns with CISA standards, transforming digital chaos into calm.

Proven Results
We’ve rebuilt defenses and transformed confidence for businesses, turning clients into heroes who outsmart threats.

What Sets Us Apart from Other Cybersecurity Companies
In a crowded field of cybersecurity firms, Leverage IT Consulting doesn’t just compete—we dominate with unmatched processes that deliver real, measurable superiority.
Rigorous Best Practices Evaluation (BPE)
We conduct deep-dive evaluations of your security posture against our battle-hardened frameworks and CISA guidelines, uncovering vulnerabilities others miss.
Relentless Proactive Testing
Our automated scans, simulated attacks, and hands-on audits run continuously, probing your systems quarterly to identify and correct security drifts immediately.
Empowering Education & Advisement
Beyond reports, we empower your team with tailored sessions, breaking down findings into actionable strategies and training staff on emerging threats.
Proven, Enduring Security
This proactive cycle means faster resolutions, fewer incidents, and a partnership that reduces breach risks by up to 75%—transforming your organization into a security-savvy powerhouse.
Other cybersecurity companies promise protection; we prove it with processes that evolve with you. Ready to experience the difference?
Our Battle-Tested 3-Step Plan to Vanquish Cyber Villains
Victory in cybersecurity comes from a clear strategy:

Expose the Weaknesses
A deep audit uncovers hidden risks and vulnerabilities, providing clear visibility.

Erect Impenetrable Barriers
We deploy custom Shield Cybersecurity Solutions—firewalls, encryption, and AI monitoring—for maximum protection.

Vigilant Defense and Rapid Strike
Continuous monitoring, instant alerts, and elite response teams neutralize threats rapidly, preventing major incidents.
Gain control with a clear, actionable security plan.
Fortress-Level Cybersecurity Built for Your World
Leverage IT Consulting offers comprehensive, evolving cybersecurity. We build unbreakable walls, not just patch holes.
Core Defenses That Stop Attacks Cold

Cybersecurity Risk Assessment
Precision scans and CISA benchmark analysis pinpoint vulnerabilities, delivering actionable insights.

Cybersecurity Consulting
Strategic guidance aligns security with your business goals, ensuring compliance and resilience.

Managed IT Security Services
Secure every connection, from VPNs to intrusion detection. Safeguard your data flow.

Managed Firewall
Your first line of defense: adaptive firewalls intelligently block intruders using AI.

Network Security Services
Secure every connection, from VPNs to intrusion detection. Safeguard your data flow.

Endpoint Detection and Response
Real-time monitoring protects devices wherever they are, catching malware in its tracks.

Penetration Testing Services
Ethical hackers simulate attacks to expose flaws before bad guys do.
Phishing causes 91% of breaches (Verizon DBIR). Our layered approach slashes that risk, with clients reporting 95% fewer incidents.
Bulletproof Backup and Recovery
Cyber attacks love data—don’t let them win. Our integrated solutions keep you ahead:

Data Backup and Recovery
Automated, encrypted backups with instant restore. A retail client recovered in hours after ransomware.

Disaster Recovery Planning
Custom blueprints for business continuity. We simulate disasters to perfect your response, minimizing downtime.

Data Encryption Solutions
Lock down sensitive info end-to-end. Compliant with GDPR and HIPAA, our encryption thwarts thieves.

“A law firm faced an APT. Our proactive monitoring flagged anomalies, and engineer-led response isolated and eradicated the threat in under an hour—no data lost. That’s the Leverage difference.
For small businesses, we scale without skimping; larger ops get bespoke integrations.
A non-profit hit by DDoS: our Shield Network Security Services deflected the assault, maintaining 100% uptime.”
In manufacturing, our Shield Endpoint Detection and Response secures IoT devices, preventing supply chain disruptions.
For accounting, our Shield Managed Firewall and encryption keep client data safe, boosting trust.
We train your team too—phishing simulations reduce click rates by 80%. Education is key to our holistic approach.
Our Shield Cybersecurity Solutions are predictive, powered by AI and human insight for unbeatable defense.

Real Heroes, Real Victories: Client Success Stories
Hear directly from those transformed by our cybersecurity solutions:
Case Study 1:
Restaurant Ransomware Redemption

"Leverage IT Consulting turned our worst day into a win—we're stronger now."
Case Study 2:
Energy Sector Siege Survival

"Leverage IT Consulting is our shield in a dangerous world."
These accounts highlight our cybersecurity firm’s unwavering prowess—delivering tangible results and real protection against evolving cyber threats. Your security, our priority.
The Catastrophic Price of Complacency
Ignoring robust cybersecurity isn’t just a risk—it’s an invitation to ruin. The fallout from a breach extends far beyond immediate financial losses, impacting every facet of your business.
Financial Devastation
The average cost of a data breach is a staggering $4.45 million (IBM). This includes investigation, recovery, and legal fees, creating a massive drain on resources.
Brand Erosion & Customer Exodus
Beyond monetary costs, a breach inflicts irreparable damage to your brand reputation. A shocking 57% of customers switch providers after a data breach (Forbes), leading to lost revenue and market share.
Operational Paralysis & Legal Fallout
The aftermath can include significant operational downtime, severe regulatory fines, and mounting lawsuits, with recovery often taking years.
Without a strong cybersecurity company, you’re not merely vulnerable; you’re actively inviting these catastrophic consequences.
Picture Your Business: Bulletproof and Booming
Envision your operations humming securely, your teams innovating freely, and your growth unchecked. With our Shield Cybersecurity Solutions, you’re not just protected—you’re empowered to thrive.
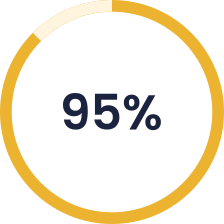
Reduced Incidents
Clients slash security incidents by 95%, minimizing disruptions and data breaches.
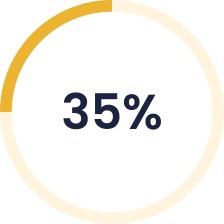
Improved Efficiency
Boost efficiency by 35% as your team focuses on innovation, not constant threats.

Complete Peace of Mind
Sleep soundly knowing your business is protected around the clock, 365 days a year.
You become the hero, commanding a fortress of success.
Quick Answers on Cybersecurity
Bulletproof Backup and Recovery
01 What Defines Top Cybersecurity Companies?
Innovation, reliability, results. We embody them, aligned with CISA for cutting-edge defense.
02 How Does CISA Influence Your Approach?
We follow Cybersecurity and Infrastructure Security Agency guidelines for zero-trust, ensuring federal-level protection for all clients.
Solutions & Services
01 How Do Cybersecurity Solutions Vary by Business Size?
Scalable from startups to enterprises. Small biz gets essentials; big ops, advanced integrations. Details in Pivotal Managed IT Security Services.
02 What if We're Already Breached?
We specialize in rapid recovery. Our Secure Disaster Recovery Planning minimizes damage—contact us immediately.
03 Do You Offer Training?
Yes, employee awareness programs reduce human-error risks by 90%. Integrated into our Shield Cybersecurity Consulting.
04 How Fast Is Your Response?
Lightning-quick: Engineers engage within 30 minutes via Shield Endpoint Detection and Response.
Related Services
Explore our arsenal of Shield Cybersecurity tools:
Advisory & Assessment
Shield Cybersecurity Consulting
Shield Cybersecurity Risk Assessment
Shield Penetration Testing Services
Resilience & Recovery
Secure Data Backup and Recovery
Secure Disaster Recovery Planning
Resilience & Recovery
Shield Endpoint Detection and Response
Shield Managed Firewall
Shield Network Security Services
Shield Data Encryption Solutions
Comprehensive Management
Arm Yourself Today—Before It's Too Late
Cyber threats evolve relentlessly; so should your defenses. As your elite cybersecurity firm, Leverage IT Consulting stands ready to secure your future.